Skeleton key
Theory
Skeleton key is a persistence attack used to set a master password on one or multiple Domain Controllers. The master password can then be used to authenticate as any user in the domain while they can still authenticate with their original password. It makes detecting this attack a difficult task since it doesn't disturb day-to-day usage in the domain.
Skeleton key injects itself into the LSASS process of a Domain Controller to create the master password. It requires Domain Admin rights and SeDebugPrivilege on the target (which are given by default to domain admins).
Since this attack is conducted in memory by reserving a region of memory with VirtualAllocEx() and by patching functions, the master password doesn't remain active after a DC reboot.
This attack currently supports NTLM and Kerberos (RC4 only) authentications. Below are a few explanation of how it works depending on the authentication protocol it injects a master key for.
The attack employs a three-steps process to create a master password for NTLM authentication.
- Reserves a memory region using
VirtualAllocEx()for thelsass.exeprocess. This memory space is used to store a modified version of the NTLM password validation functionMsvpPasswordValidate(). - Attaches itself to the
lsass.exeprocess and locatesMsvpSamValidate()(authentication function) fromMSV1_0.dll(which is the DLL in charge of NTLM authentication). - Finds the call to
MsvpPasswordValidate()(password validation function) inMsvpSamValidate()and patches it to make it point to the modifiedMsvpPasswordValidate()stored in the memory region from step 1.
When called, the modified version of MsvpPasswordValidate() first calls the original MsvpPasswordValidate(): therefore if a legitimate authentication is tried, it will succeed.
If the original MsvpPasswordValidate() fails, the modified version will call the originalMsvpPasswordValidate() again but will make it compare password hash supplied during the authentication with the hash of the master password set when launching the attack (i.e. mimikatz by default when using Mimikatz for this attack).
Practice
Skeleton Key can be injected with the misc::skeleton command in Mimikatz. It works in every 64-bits Windows Server version up to 2019 (included).
Mimikatz must be either launched as NT-AUTHORITY\SYSTEM or be executed with a domain admin account on the Domain Controller. For the latter, debug privileges (SeDebugPrivilege) must be set for Mimikatz to work. This can be done with the privilege::debug command.
mimikatz "privilege::debug" "misc::skeleton"By default, the master password injected is mimikatz.
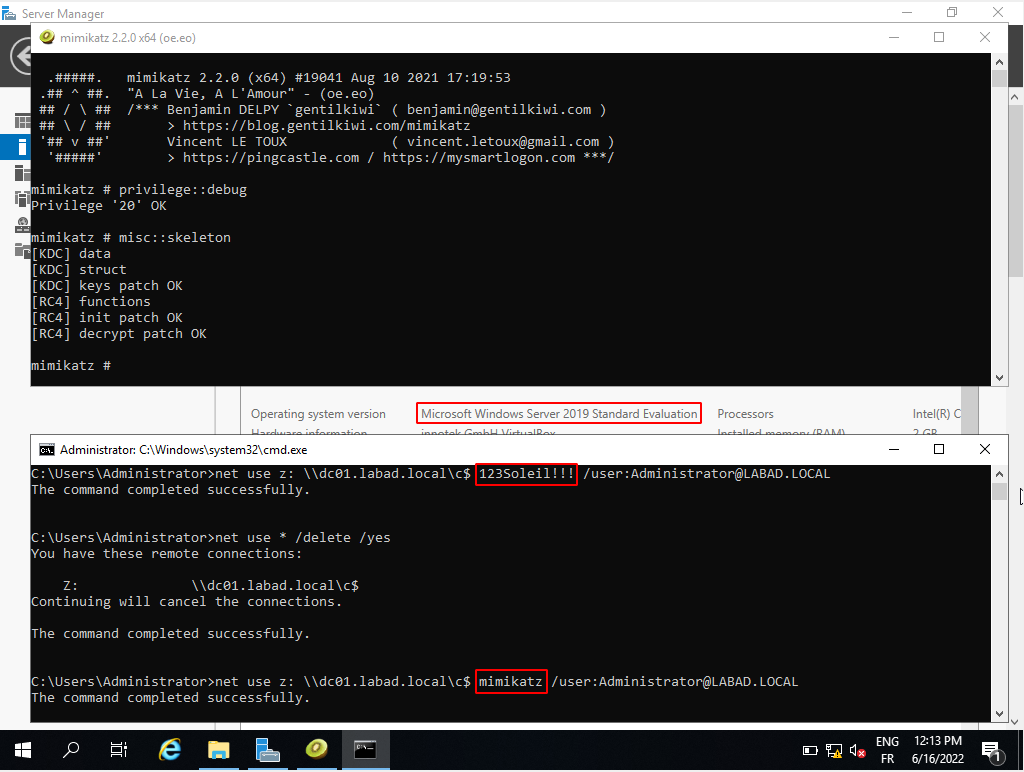
Skeleton key injection and usage illustration on a Windows Server 2019
Resources
https://adsecurity.org/?p=1255
https://pentestlab.blog/2018/04/10/skeleton-key
https://www.virusbulletin.com/uploads/pdf/magazine/2016/vb201601-skeleton-key.pdf
